Overview
This article reviews a demonstration of Betsy™ and the Private Island ® open source project for FPGA-based networking. The demonstration highlights the flexibility and power of the Verilog project on low cost hardware by showing Betsy both as a network tap and a highly configurable packet filter.
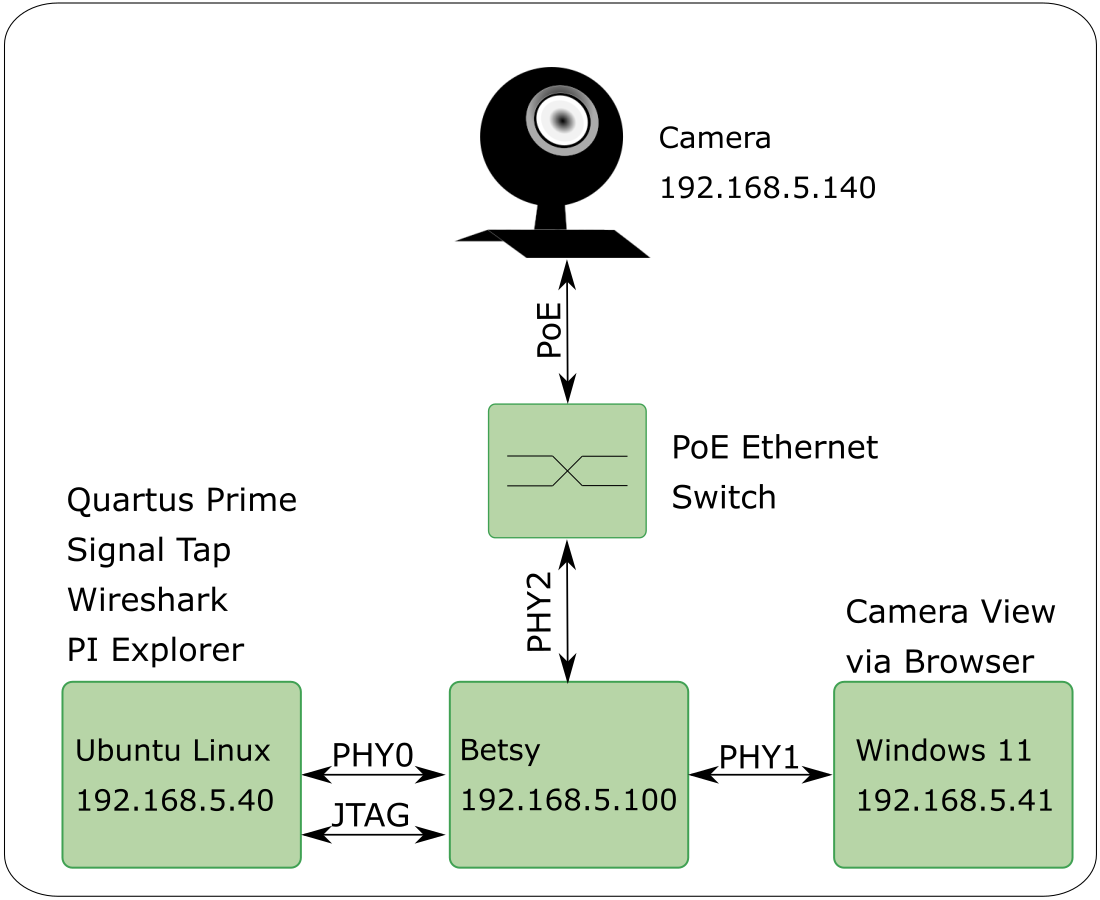
As depicted in the figure below, the Betsy maker board switches data between three different Ethernet ports:
- PHY0: An Ubuntu Linux 24.04 laptop
- PHY1: A Windows 11 laptop
- PHY2: An inexpensive 5MP PoE security camera
The Ubuntu Linux laptop also has a USB-based JTAG connection to support the Altera Quartus Programmer and Signal Tap Logic Analyzer applications.
By default, Betsy acts as a network tap and switches all data exchanged between the Win 11 laptop and camera to the Ubuntu Linux laptop. Customizable packet filtering is also used to drop all data transmitted by the camera based on its source MAC address. The packet filter is programmed and enabled using the companion open-source PI Explorer web-based application.
The Altera (Cyclone 10 LP based) Quartus Project for this Betsy demonstration has minimal customizations that include customized MAC address filtering using the packet filter between PHY2 and PHY1.
Betsy FPGA-based Maker Board
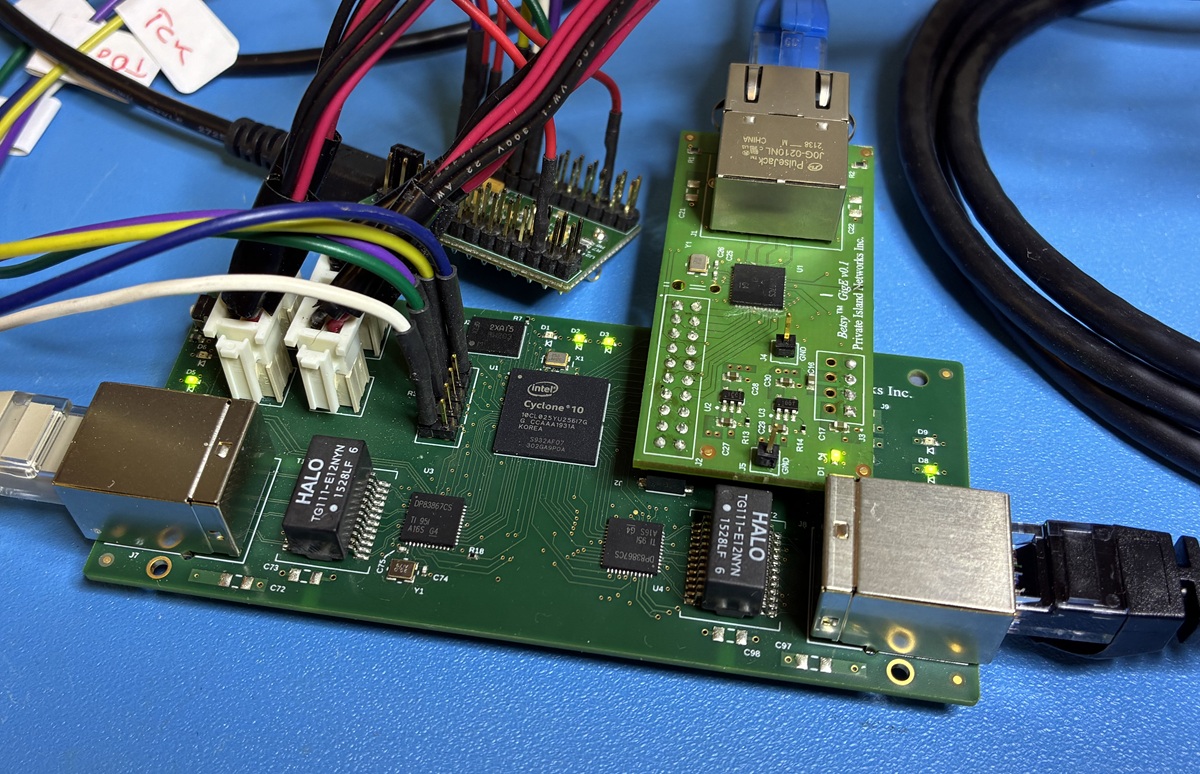
Figure 2 below shows the Betsy system with its GigE Daughter Board on the lab bench. Also shown is an FTDI Mini Module used as the JTAG dongle.
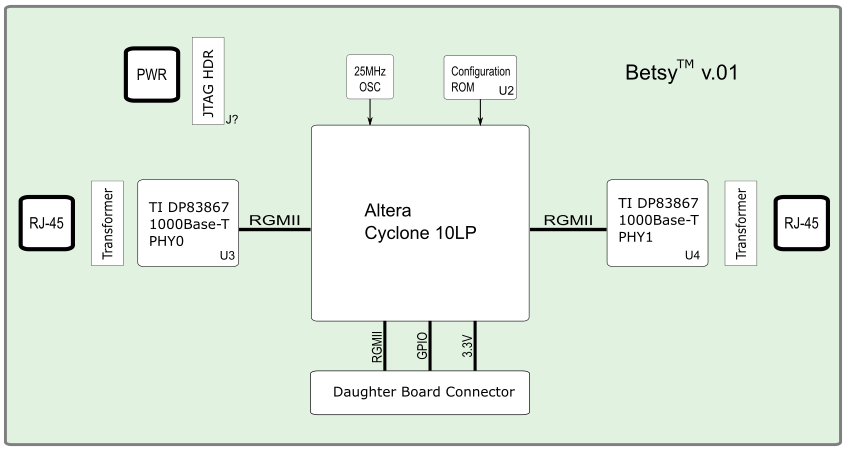
The next figure provides a block diagram of the Betsy maker board prototype (v0.1), which is being used for the current beta trial.
Private Island Open Source Project
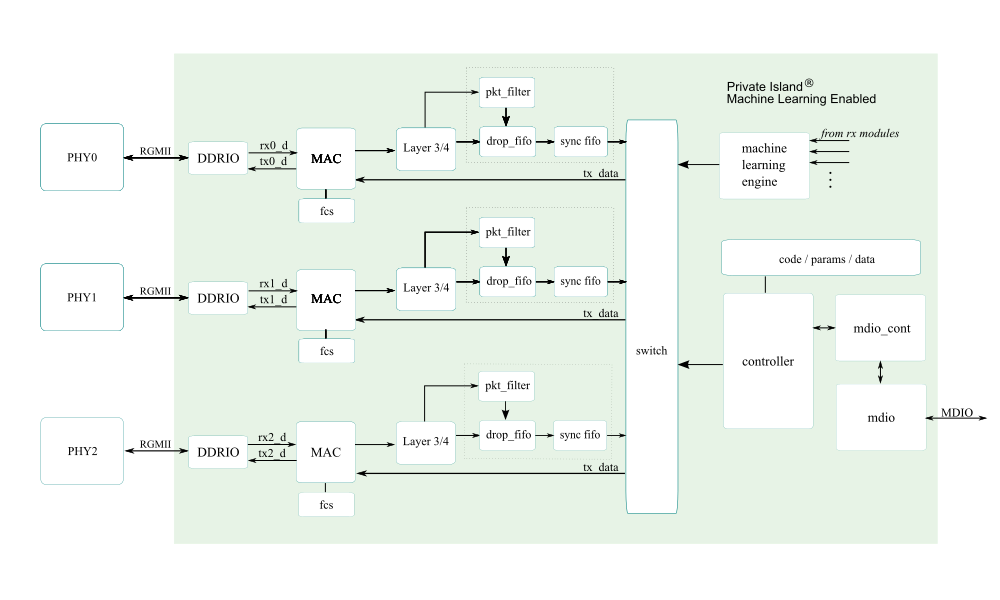
Figure 4 below shows a block diagram of the default Private Island configuration and Verilog module hierarchy for Betsy. Note that the bottom pkt_filter and drop_fifo modules are responsible for dropping the camera transmit packets.
Ubuntu Linux Screenshots
A Wireshark screenshot is shown below from the Ubuntu Linux laptop, which is being used to receive the network tap data. This shows the exchange between the camera and the Win 11 laptop.
Consider the power of such a network tap and filter combination if the Win 11 PC was replaced by a network firewall or router in Figure 1 above.
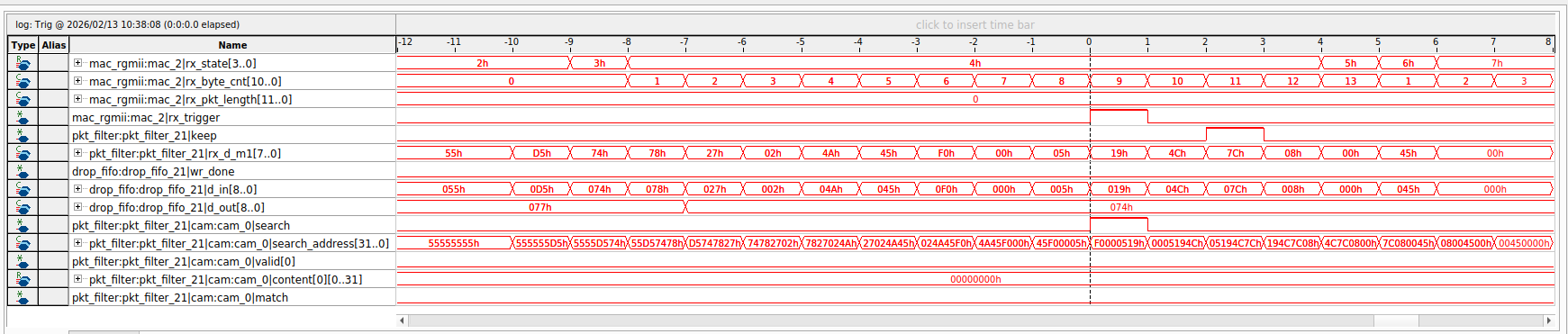
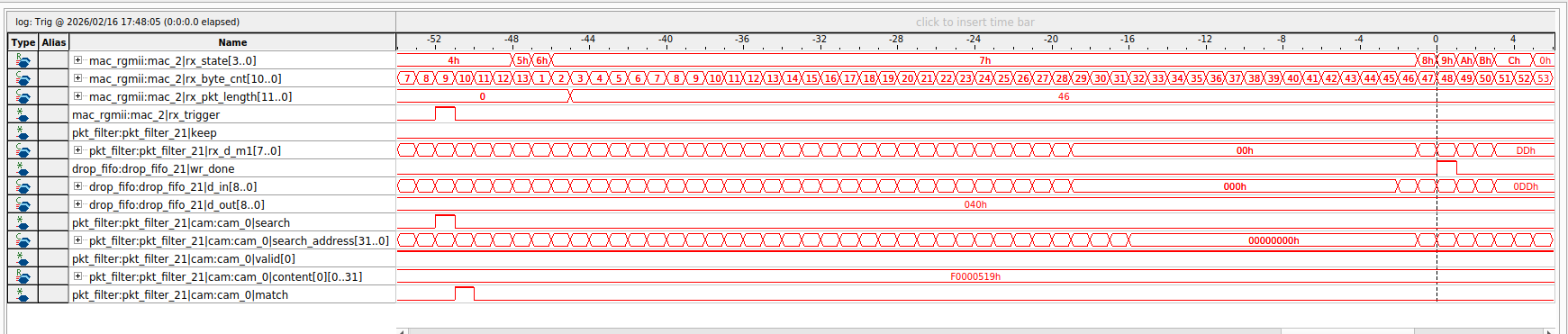
The Signal Tap logic analyzer screenshot below shows some of the critical Verilog variables involved in the CAM search for a specific source MAC address. At this point, the CAM has not been programmed, so there is no match resulting from the CAM search.
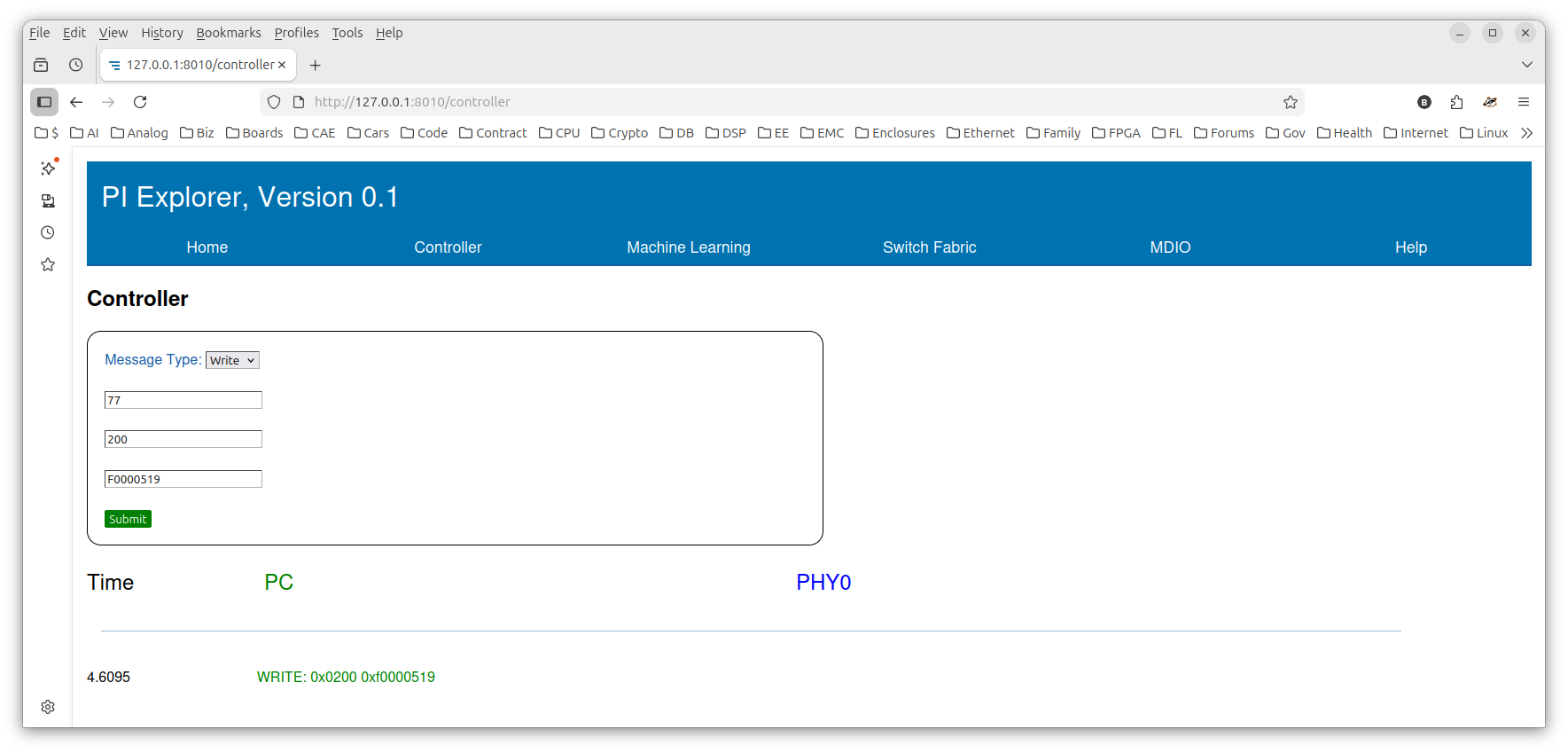
The next screenshot shows the Python-based Web application PI Explorer. This aiohttp-based Web application supports configuring and querying the Betsy board via the LAN using a standard browser (e.g., Firefox). The source for PI Explorer will be hosted on this website soon.
Shown below is a write to the pkt_filter module to program the first CAM entry with four of the six address bytes for the camera's source MAC address.
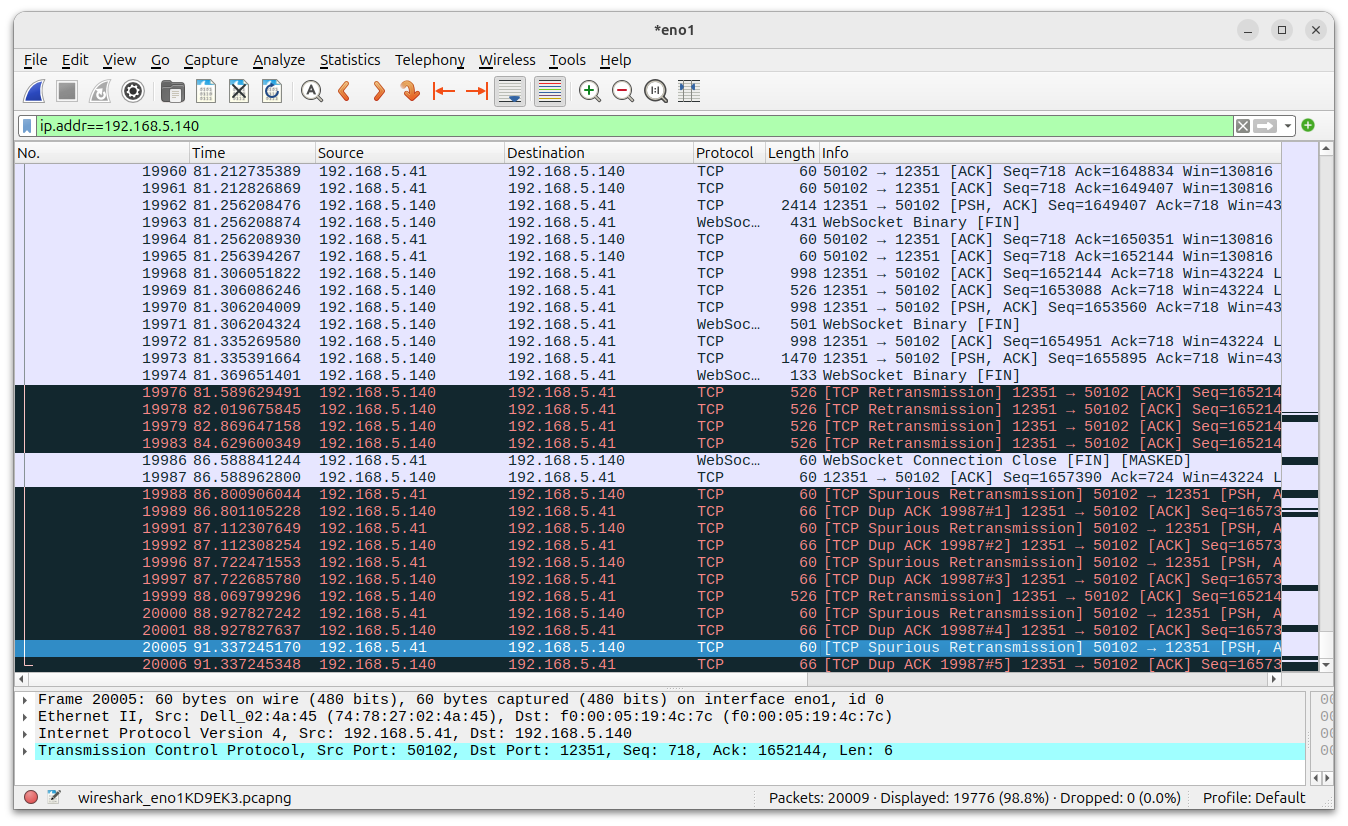
The Wireshark screenshot below conveys that the existing TCP connections between the camera and the Win 11 laptop are no longer active (each side sends retransmission packets).
The last screenshot below shows a Signal Tap trace that confirms data transmitted from the camera is being dropped at the drop_fifo module. This is a good example of a true and reliable confirmation that data is purposefully dropped in the network.
Additional information will soon be provided to this article to detail the specific changes made to the default Private Island project to support this demonstration.





